Our website is made possible by displaying online advertisements to our visitors.
Please consider supporting us by disabling your ad blocker.
Stacheldraht
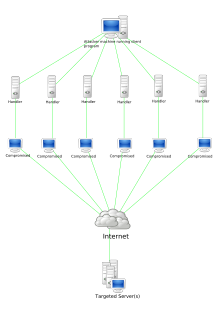 Stacheldraht attack diagram | |
| Original author(s) | "random" |
|---|---|
| Initial release | 1999[1] |
| Stable release | 4
|
| Repository | https://packetstormsecurity.com/distributed/stachel.tgz |
| Written in | C |
| Operating system | Linux, Solaris |
| Size | 36 kB |
| Type | Botnet |
| Website | packetstormsecurity |
Stacheldraht (German for "barbed wire") is malware which performs a distributed denial-of-service (DDoS) attack. It was written by "Thomas Stacheldraht", a member of the Austrian hacker group TESO. It was first released in 1999.[1]
Stacheldraht uses a number of different denial-of-service (DoS) attack methods, including Ping flood, UDP flood, TCP SYN flood, and Smurf attack. Further, it can detect and automatically enable source address forgery. Adding encryption, it combines features of Trinoo and of Tribe Flood Network. The software runs on both Linux and Solaris.[1]
Stacheldraht was later superseded by Blitzkrieg, which was maintained by "random" and a loose group of associates.[citation needed]
- ^ a b c Cheng, Geoffrey. "Malware FAQ: Analysis on DDOS tool Stacheldraht v1.666". GIAC. SANS Institute. Retrieved 15 May 2021.
Previous Page Next Page


